Viruses are getting smarter
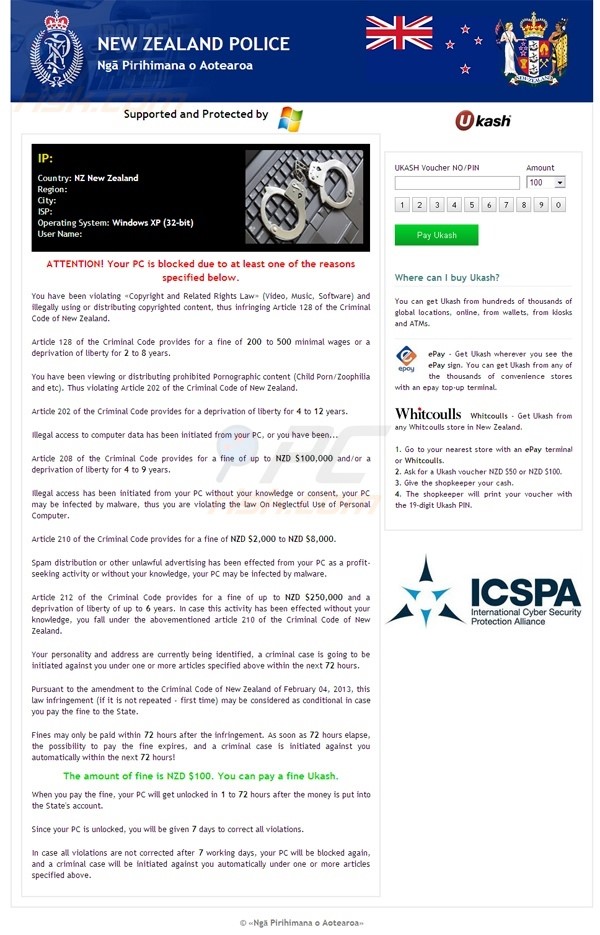
What would your first thought be seeing the above on your computer, laptop or cellphone? Would you start to wonder “What has my family been looking at?” or “What have I come across browsing the internet by mistake?”
Within the last year we have been seeing an increasing trend in viruses called Ransomware.
‘Ransomware’ is a type of malware/virus that attempts to extort money from a computer user by infecting and taking control of the victim’s computer, cell-phone, or the files or documents stored on it. Typically, the Ransomware will either ‘lock’ the computer to prevent normal usage, or encrypt the documents and files on it to prevent access to the saved data.
The ransom demand will then be displayed, usually either via a text file or as a webpage in the web browser. This type of malware leverages the victim’s surprise, embarrassment and/or fear to push them into paying the ransom demanded. Ransomware may arrive as part of another malware’s payload, or may be delivered by an exploit kit such as Blackhole, which exploits vulnerabilities on the affected computer, device to silently install and execute the malware.
In almost all cases, payment of the ransom still does not restore the computer to normal use. As such, we strongly recommend that no payment be made and give us a call straight away. You may have never heard of this type of virus or even been affected. Prevention is simple, make sure to have up-to-date antivirus (Eset nod antivirus for example). Stay away from unsafe websites (Adult content, kids free game downloads or pirated music, movies or tv shows). Good idea if you have kids is to take interest in what they do online so they and your computers are safe.
Backups are also highly recommended; there was a case in America recently when a police station themselves was hit with another type of randomware that encrypted all computers and network drives, files. Due to this police station having no backup, the police had to pay the ransom (At least the criminals were honest enough to send the police the de-crypt code to unlock the police station pcs !).
Remember we are here to help you regarding any Information Technology issues like viruses or malware. We are but a phone call away.
So if you’re in need of some help with Viruses, or even just some free friendly advice, get in touch with us, 6-370 8093.
To discuss how Tech Solutions can help call us on 0800 878 878 or email office@techs.co.nz.