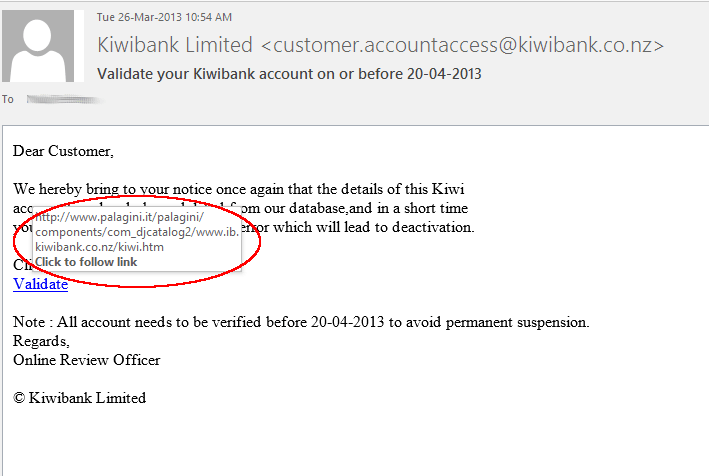
Facebook Security Settings
The Facebook Settings You Should Check
This year (2013) Facebook have made several changes to it’s privacy policy and your settings, if you haven’t looked at your profile settings lately then now would be a good time to do it.
If you’re like the most of us here, you like to share your social life with a select group of friends and not the rest of the world, there are a few settings you should make sure are in place going forward.
See your profile as others see it
First thing you should do is see how the rest of the world (except your friends) see your profile. Click the gear icon in the upper right-hand corner of your Facebook page and select Privacy Settings, now click Timeline and Tagging in the left pane, now click View As to the right of Review what other people see on your timeline.
If you’ve limited access to your timeline to friends only, the public will see only your profile and cover photos, a link for contacting you (which you can limit to friends of friends), the people you’re following, and the groups you belong to. A tip here, you can view your timeline as a specific Facebook user, click View as Specific Person at the top of the window and enter the person’s name.
Privacy Settings
You’ll find these as a drop-down option when you click the gear icon in the upper right-hand corner of your Facebook page on the Web. Here, you can tailor the audience for your posts. You can go back and make all your posts private in this section, access the Activity Log (see the next section), and determine how widely you want to distribute future posts by default.
You can also set who can contact you and how. This is where FB removed the feature “look up my timeline by name”, but you can still control who finds you by searching an email or phone number. We recommend you set these to “Friends” Only, and turn the Do you want other search engines to link to your timeline – Off.
Activity Log
In your activity log, you can view and edit your posts, messages, posts you’ve been tagged in, photos, likes, and comments. You can edit or delete any activity dating back to when you first joined Facebook. You can access your Activity Log via Privacy Settings – Use Activity Log.
Timeline and Tag Settings
After you’ve clicked into your privacy settings, look at the left-hand column for finer grained control of your Timeline and tags. If you want to know who’s tagging you in posts before your name publicly appears on someone’s timeline — and deny them if you choose — make sure the “review posts” setting is turned on. We also recommend you turn on “Review tags people add to your own posts before the tags appear on Facebook” and that you set “Who sees tag suggestions when photos that look like you are uploaded?” to No One.
We hope this helps and if you have any questions about Facebook security, or even just some free friendly advice, get in touch with us, 6-370 8093.