Create an email signature onto your iPhone
Today’s email signatures contain a lot more than just your name and contact details. Links to websites, Facebook, Twitter account and the ubiquitous legal disclaimers along with your company’s branding give clients the information they need.
Many of you have this on your main computer email system but when it comes to your mobile devices “sent from my IPhone” is as flash as it gets…
Not only can you have the same email signature on your iPhone/iPad but you can create multiple email signatures for each account that you access (business/personal/rental etc.).
Either send yourself an email message from your computer or device that already has the desired signature set up on it or check you’re sent items for one.
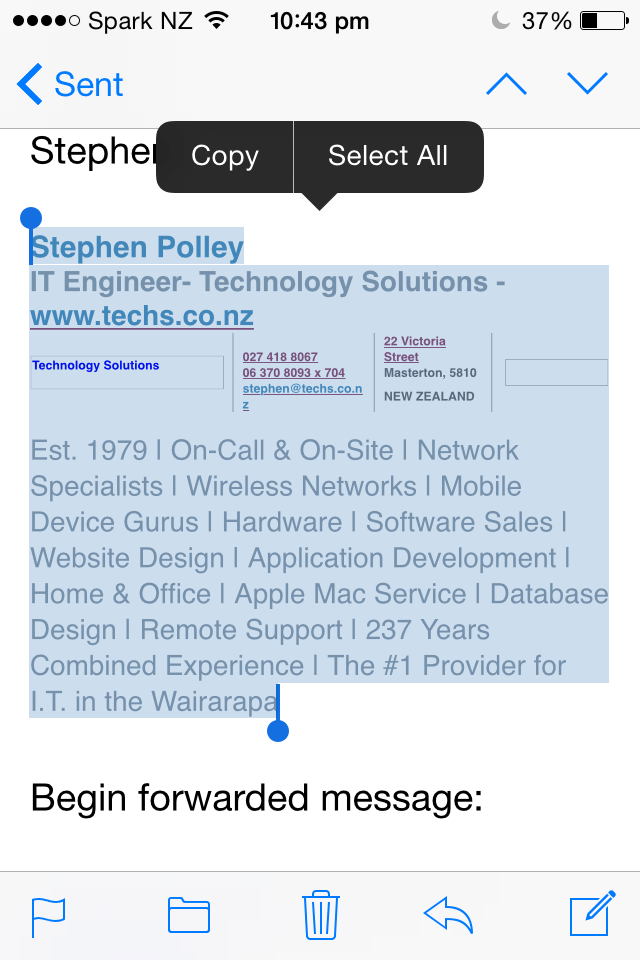
- Open the email in the Mail app on your iPhone/iPad.
- Tap and hold down on the signature in order to bring up the blue selection tool. Move the anchors so you have the entire signature highlighted.
- Tap on Copy.
- Press the Home button to return to your Home screen.
- Launch the Settings app.
- Tap on Mail, Contacts, Calendars.
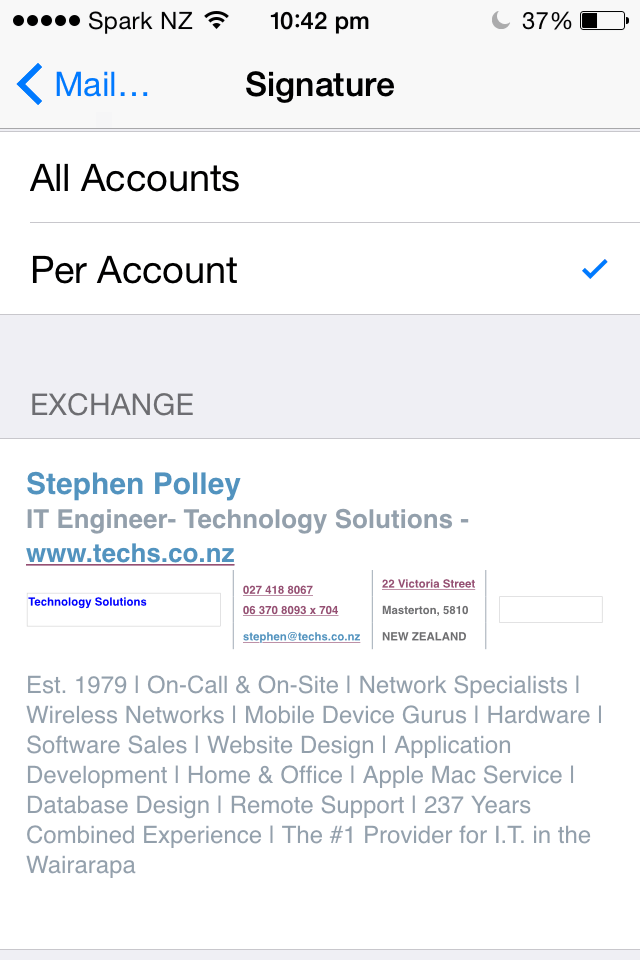
- Scroll down to Signature under the Mail section.
- Tap on the account you’d like to add the signature to if you have multiple signatures set up Per Account.
- Delete the contents.
- Tap and hold in the signature field to bring up the selection tool again.
- Tap Paste in the popup menu.
- You may see a strangely formatted version of your signature but here’s the magic…
- Shake your iPhone briefly and tap Undo in order to remove the automatic formatting Apple may have done.
- This will bring back any colors or other HTML content that may not have shown up in the original paste. Et Voila.
If you want to know more call us on 0800 878 878 or email stephen@techs.co.nz.